Getting a brand new bank card quantity is comparatively straightforward, however you’ll be able to’t get a brand new genome.
In October 2023, 23andMe skilled an information breach ensuing from a credential stuffing assault. On this cyberattack, hackers exploit reused usernames and passwords obtained from earlier knowledge leaks to achieve unauthorized entry to person accounts. Initially, roughly 14,000 accounts had been compromised. It uncovered the delicate private and genetic knowledge of about 5.5 million customers and an extra 1.4 million profiles.
A hacker group known as “Golem ” stole probably the most intimate private knowledge of 23andMe’s subscribers, together with full names, profile images, beginning years, places, household surnames, grandparents’ birthplaces, ethnicity estimates, extremely particular genetic data, and different private particulars that customers had opted to share. The information was freely out there in giant textual content information to anybody who knew the place to look on the darkish net.
To grasp the implications of this assault, we’ll have to look again only a bit. Revolutionizing Private Information Entry
The genetic testing firm 23andMe was one of many first firms to permit “regular individuals” to achieve perception into the secrets and techniques held of their genomes. Nearly in a single day, utilizing a few of the most superior know-how on the time, individuals may see genetic traits starting from eye shade to illness predisposition. Like many advances, customized entry to delicate genetic knowledge preceded critical conversations about these knowledge’s dangers. 23andMe efficiently supplied the world entry to a few of the most delicate private knowledge (our genomes) nicely earlier than we may absolutely perceive the safety and privateness implications.
Whereas life sciences corporations are extremely superior of their utility of know-how, they don’t seem to be an trade recognized for his or her management in cybersecurity. The tempo of analysis or the stress to get to market with a brand new product usually outpaces the safety implications, and far of the particular safety and compliance work is finished after the actual fact. Massive firms and the biggest educational establishments have budgets to guard themselves and research compliance implications, akin to GDPR and HIPAA, earlier than a brand new know-how is dropped at market. Smaller biotech corporations on the innovative usually can’t afford or don’t finances for these steps, inserting their useful resource extra round getting their product out.
Quick innovation, delicate mental property, and evolving laws all work collectively to drive the severity of this example. Regardless of dealing with a few of the most respected knowledge on this planet—starting from proprietary drug formulation to affected person data—many life sciences corporations nonetheless lag in cybersecurity maturity.
In response to current trade intelligence:
• Cybercriminals aggressively goal biotech and pharmaceutical firms for mental property theft, extortion, and espionage.
• Provide chain threat is a rising concern, as many life sciences corporations depend on third-party analysis, storage, and cloud infrastructure, every including a layer of vulnerability.
• Identification-based assaults are surging, fueled by weak credential administration and an absence of id governance—a niche highlighted by IBM’s X-Power report, which famous that cloud account credentials now make up 90% of cloud-related property offered on the darkish net.
Life sciences organizations are custodians of extremely delicate knowledge—mental property, medical trial outcomes, genetic data, and affected person data. On the similar time, these organizations are topic to much less uniform enforcement than healthcare suppliers. Healthcare organizations dealing straight with PHI are topic to aggressive HIPAA enforcement by the OCR (Workplace for Civil Rights), with breaches resulting in important fines and mandated corrective motion plans. Life sciences firms usually straddle the road between analysis and care supply and have a tendency in the direction of their analysis and growth roots.
My Time in Life Sciences
Because the Chief Data Officer for the biotechnology agency Built-in DNA Expertise (IDT) for over twenty years, I used to be reminded of those dangers every day. Our know-how workforce ensured that the digital methods behind ordering, producing, and delivering artificial DNA and RNA labored securely and reliably. Our agency supported over 80,000 purchasers in educational and company life sciences. From the largest pharma firms to the smallest analysis labs, our merchandise gave us visibility into your entire life sciences trade.
We confronted cyber threats from activist teams and nation-state actors alike. Nameless has publicly acknowledged its opposition to Genetically Modified Organisms (GMOs) and regularly attacked clients. A lot of our researchers had shut ties to their analysis amenities in China, a few of whom competed straight in opposition to our purchasers.
Deep Dive – 23andMe’s Breach Information
We wanted to research what was taken from 23andMe to know the assault’s strategies and impression. Cybersecurity corporations are sometimes requested to analysis the implications of those assaults and the exfiltrated breach knowledge. Intently analyzing the information offered by the hackers helps us defend each the person shopper and the general trade affected. For instance, a bank card breach from a single gasoline station might impression a number of monetary establishments that originally issued these playing cards. Forensic investigation of bank card information offers priceless insights to diagnose the supply of the difficulty and forestall future breaches.
An instance of knowledge from the 23andMe breach posted on the Darkish Internet.
Evaluation of the 23andMe breach knowledge uncovered some unlikely assault victims – together with Elon Musk. Whereas there isn’t any technique to verify that that is Elon Musk’s knowledge with out an precise genetic pattern, he’s referenced in a number of areas of the breach. If these are his knowledge, Elon is as a lot a sufferer of this breach as I’m. (Sure, 23andMe has my private knowledge as nicely.)
The breach contained a mission that a mission evaluating Elon Musk’s personal data to that of over a thousand people. This analysis checked out a number of patterns of genetic areas inside particular chromosomes for varied items of extremely delicate data. These knowledge present insights into predisposition to illness and distinctive human traits, akin to mind growth and metabolism.
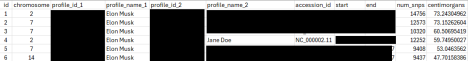
Within the instance above, a search was leaked evaluating Elon Musk by evaluating areas of his second, seventh, and fourteenth chromosomes with a number of thousand different individuals within the 23andMe knowledge. The matches (redacted) are listed as profile_name_2 and embrace the precise areas studied. Centimorgans (cM) is a measure of genetic complementarity, and the upper the quantity, the higher the match. For
reference, an equivalent twin would share 100% of their DNA, leading to a 3,600-3,800 centimorgan rating. The match with the primary profile is most per a distant familial relationship (like third–4th cousins, or much more distant if from an endogamous inhabitants like Ashkenazi Jews or Amish). It’s not shut sufficient for half-siblings, first cousins, and even 2nd cousins—these would sometimes share a number of segments totaling 200–800+ cM.
The outcomes of an awfully detailed and private comparability of Elon Musk’s genome had been out there on-line. Hackers may probably use this knowledge for any variety of illicit actions, together with blackmail, analysis exploitation, discrimination, and social manipulation.
As a result of scope of this cybersecurity breach, 23andMe filed for Chapter 11 chapter safety on March 23, 2025, and along with the chapter submitting, co-founder and CEO Anne Wojcicki resigned. The corporate plans to pursue a court-supervised sale of its property to maximise enterprise worth. Whether or not the information turns into out there to a menace actor through the breach or a future breach of the corporate buying 23andMe’s property (the information), the cat is out of the bag. As soon as genetic knowledge is disseminated, it’s unimaginable to regulate using the data.
Difficult Issues, Less complicated Options
The unlucky demise of 23andMe is a canary within the coal mine. The life sciences trade should decide to defending these knowledge. That is finest achieved in 2025 by mastering the basics—the core constructing blocks of cybersecurity hygiene. These aren’t glamorous, however they’re terribly efficient. Most breaches immediately are attributable to primary missteps: weak passwords, unpatched methods, and poorly configured entry controls. Life sciences corporations can stop practically all however probably the most superior nation-state-level assaults by specializing in fundamentals.
Identification and entry administration (IAM) is a stable first step in life sciences to develop simpler cybersecurity hygiene. This implies guaranteeing that each person has solely the mandatory entry—and nothing extra. Implementing sturdy authentication strategies like multi-factor authentication (MFA) and adopting least-privilege entry fashions prevents dangerous actors from exploiting stolen or weak credentials, which stay among the many prime causes of breaches, in keeping with the Verizon Information Breach Investigation Report and IBM X-Power studies.
Second, patch and vulnerability administration have to be operationalized. Most exploited vulnerabilities are recognized and patchable. Life sciences organizations should set up a routine cadence to determine, prioritize, and remediate these weaknesses. Even higher, they might automate it. That is the place governance is available in—join patch administration to accountability, making it a tracked KPI at each the IT and govt ranges.
Subsequent, third-party and provide chain safety is particularly crucial within the life sciences trade, the place R&D and knowledge dealing with usually contain complicated webs of CROs, labs, and digital platforms. Life sciences organizations ought to carry out due diligence on companions, demand safety attestations (like SOC 2 or HITRUST), and limit third-party entry by segmentation and nil belief ideas.
To combine these fundamentals into organizational governance, life sciences corporations ought to:
• Elevate cybersecurity on the board and govt ranges as a standing agenda merchandise. • Appoint a robust Chief Data Safety Officer (CISO) or digital CISO to supervise technique and implementation.
• Embed cybersecurity into product growth lifecycles—particularly for corporations growing digital well being instruments or platforms.
• Spend money on ongoing worker cybersecurity consciousness and coaching, specializing in real-world phishing simulations and knowledge dealing with insurance policies.
• Align with frameworks like NIST CSF, HITRUST, or ISO 27001 to make sure consistency and audit readiness.
The federal government can even create uniform expectations and drive the adoption of finest practices by regulation, incentives, and by sharing menace intelligence. Sadly, industries which might be self-regulated don’t have that menace of enforcement from businesses just like the OCR, so they have an inclination to disregard the dangers and gamble on the possibility that they received’t have a breach.
In Abstract
The 23andMe breach is a wake-up name for shoppers and your entire life sciences trade. It underscores what many people have recognized for years: cybersecurity isn’t a technical checkbox—it’s a basic pillar of belief. Life science organizations should rise to the problem as stewards of a few of the most delicate knowledge. The instruments can be found. The experience exists. What’s wanted now could be management.
In an period the place our DNA could be digitized, saved, and stolen, defending the information should grow to be as essential as gathering it. The way forward for customized medication isn’t nearly scientific breakthroughs—it’s about preserving the Belief that makes these breakthroughs potential.
About Aaron R. Warner, CEO of ProCirucular
Aaron R. Warner is the founder and CEO of ProCircular, an data Safety and Privateness agency specializing in midsized companies. A former CIO and CTO of Built-in DNA Expertise, he’s spent greater than twenty years working in IT and InfoSec. Mr. Warner is a Licensed Data Methods Safety Skilled (CISSP) and authorized Securiity+ engineer, and a full member of the FBI/DHS Infragard partnership.